
It's anyone's guess how the FBI thinks it might get into the iPhone used by the San Bernardino terrorist.
The FBI said this week that it is cautiously optimistic after an outside party told investigators how to do it.
What's the method? And who told them how to do it? The FBI won't say.
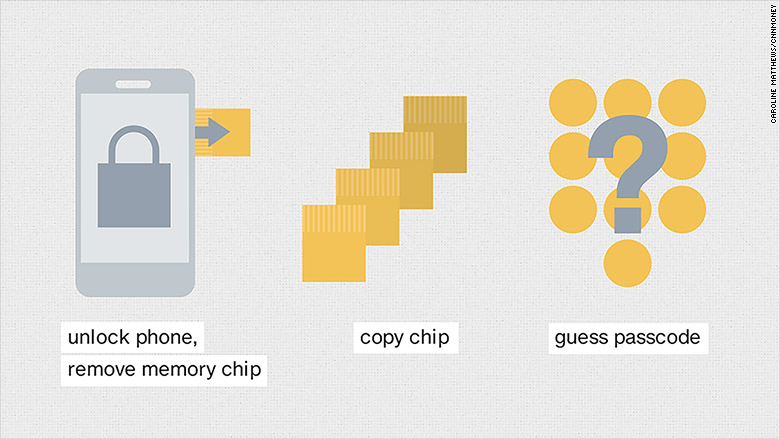
But that hasn't stopped the security world from taking educated guesses. The solution they keep coming back to is the same one cybersecurity experts have been talking about for weeks: Cracking open the phone, taking out the memory chip, copying it and guessing the passcode over and over again.
That is the likeliest of ways in, according to Jonathan Zdziarski, a computer security expert who specializes in Apple products. It would get the FBI around a crucial problem: The iPhone 5C is permanently locked. If its self-destruct feature is turned on, it will erase its key after 10 incorrect passcode guesses.
This hack was thrust into the public discussion at a House Judiciary Committee hearing on March 1, when Representative Darrel Issa chastised FBI director James Comey for not considering it.
"If you haven't asked that question, how can you come before this committee and a federal judge and demand that someone invent something?" Issa asked Comey.
Comey admitted during the hearing that the FBI hadn't asked Apple about that method, nor did he "fully even understand" it. But he said at the time that he was "fully open to ideas."
Apple vs. the FBI ... in 2 minutes
Here's how the hack would work: The FBI would separate the memory chip from the phone and make a copy of it.
To break the memory chip's encryption, the FBI would have to do some trial and error: Investigators would pair each memory chip with the phone's encryption chip, guessing a handful of passwords before the encryption chip timed them out or wiped the memory.
Then, the FBI would swap out the memory chip for another copy, and guess a few more passcodes. Eventually, they would arrive at the correct passcode and gain access.
CNNMoney spoke to several security experts who agreed that the memory trick was a possible solution. But one said he's not even sure it's the FBI's likeliest path to entry. Another cast doubt on the method, saying it involves soldering, which is a giant pain.
But Zdziarski says it's the most likely tool the FBI is using, because it is "a fairly straightforward technique" that could be accomplished by a third-party forensic company within the time frame the FBI set up: The government has until April 5 to notify the court whether the hack worked.
Even if Zdziarski and the broad security community is right about the memory hack, it's not even clear that the method will work.
And even if it does work, it wouldn't necessarily help law enforcement in its broader fight to break into encrypted iPhones. The newer iPhone 6 and 6S models would not allow investigators to use such a method to extract a suspect's files, because they were built more securely.
-- Jose Pagliery and Laurie Segall contributed reporting to this story

