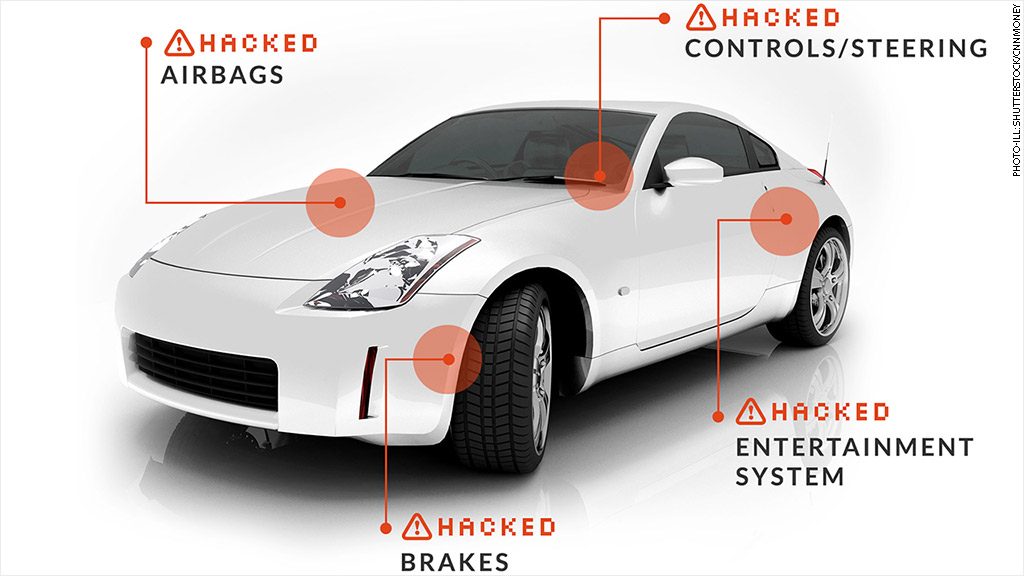
Imagine driving down the highway at 70 miles per hour, when suddenly the wheel turns hard right. You crash. And it was because someone hacked your car.
It's not far-fetched science fiction. It's the near-term future today's hackers are warning about.
Most people aren't aware their cars are already high-tech computers. And now we're networking them by giving them wireless connectivity. Yet there's a danger to turning your car into a smartphone on wheels: It makes them a powerful target for hackers.
Interviews with automakers, suppliers and security advisers reveal a major problem with the new wave of "connected" cars: The inside of your car has ancient technology that presents a security risk.
- The 50 to 100 tiny computers that control your steering, acceleration and brakes are really dumb. They rarely conduct authentication, checking whether that message is really coming from you. An outsider can send them commands.
- The computer code in cars is outdated. It's similar to the on/off switches used in industrial controls. It's easily manipulated.
- Much like the human central nervous system, every electronic part inside a car is connected to a central spine. Tap one part, you can likely reach any other.
"The protocol and internal parts of the car were never meant to be connected to anything," said Joe Klein, a researcher at security firm Disrupt6.
Cars' computers were built safely enough back in the 1990s, when the car was a closed box. But their architecture won't hold up as we hook them up to the Internet.
Related story: Tesla car doors can be hacked
Consider the level of complexity of modern day cars -- and the chance for a screw up. The space ship that put humans on the moon, Apollo 11, had 145,000 lines of computer code. The Android operating system has 12 million. A modern car? Easily 100 million lines of code.
"Auto manufacturers are not up to speed," said Ed Adams, a researcher at Security Innovation, a company that tests the safety of automobiles. "They're just behind the times. Car software is not built to the same standards as, say, a bank application. Or software coming out of Microsoft."
The nightmare scenario: Hackers access your car's core controls by breaching its Internet-connected entertainment system and tamper with your brakes.

Hackers have already proven that scenario can happen. Security engineers Charlie Miller and Chris Valasek demonstrated last year how they could hijack control of a car by connecting laptops to the dashboard.
But cars are going wireless. The next generation of Audi and Tesla (TSLA) automobiles are connected to the AT&T (T) network. Wires won't be needed to hack them.
Related: Cybersecurity: How safe are you?
Meanwhile, there's a growing potential for car malware. Makers of "infotainment" systems -- dashboards that function like a tablet -- are racing to add fun apps. But if automobiles' internal electronics remain insecure, downloading a malicious app to your car could spell big trouble. That's why auto suppliers are taking initiative.
Harman (HAR) makes Bluetooth audio devices that end up in BMWs, Hyundais, Mercedes-Benzes and others. The company is adding its own layers of security by using software to virtually separate the entertainment system from the car's network. It raises the bar of difficulty for a hacker to use a music app to worm his way into your steering controls.
Sachin Lawande leads Harman's infotainment division and justifies its initiative: "The assumption we're making is that it'll take a while for the auto industry to move to a more secure internal network than what we have today."
Continental, one of the world's three major auto parts suppliers, is partnering with IBM (IBM) and Cisco (CSCO) to make firewalls that control the information flow between the car's devices. Until it gets security all figured out, the German company is holding back from adding full Internet connectivity features, such as real-time information from the engine that alerts the local car shop ahead of time.
"Without having a good firewall or security in place, I can't go to the auto manufacturer and say, 'Let me have access to information from engine management,'" said Tejas Desai, Continental's head of interior electronics for North America.
Related story: Half of American adults hacked this year
For their part, car manufacturers are working on these problems too.
Ford (F) hardware has built-in firewalls to prevent malicious tampering, and the company has a team of noble hackers constantly probing for weaknesses.
Toyota (TM) does all that too, plus it embeds security chips in the tiny computers throughout the car, narrowing how they communicate and lessening the chance of outsider interference. The company even has forward-thinking plans this year to visit the world's largest hacker conference, Black Hat.
It should be no surprise that Tesla (TSLA) is ahead of the pack. The Model S is the most advanced and connected car currently available. It's worth noting the company's mature approach to addressing vulnerabilities. Instead of hunting down hackers who spot weaknesses, they reward them with an "Information Security" badge that works like a Willy Wonka golden ticket, granting exclusive access to Tesla's factory in Fremont, Calif. The company recently sent one to a British hacker who goes by Jon of Bitquark.
But there remains a glaring, three-prong problem beneath all of these security approaches. The car's many little computers will continue to be connected to one another. All auto makers are moving toward Internet-connected cars. And no one is willing to physically separate the core controls from the car's wireless communication hub.
That's partly because federal regulators will soon demand that cars automatically relay information wirelessly to one another as part of the U.S. government's vehicle-to-vehicle communication program. Those car-to-car messages will one day be able to engage brakes -- or your steering wheel.
If decades of computer hacking has shown us anything, it's that smart people will find a way to break in and bounce around.
Scott Morrison, who oversees automotive app engineering at CA Technologies (CA), acknowledged all of these problems exist and said the industry knows what's on the line.
"They're very aware they don't get second chances on this, so they're taking it very seriously," he said.

