Experts don't know where it came from, and aren't quite sure what it does.
But they do know this: a newly-uncovered cybersecurity threat wasn't your typical credit-card stealing operation. It appears to be a government spying tool, and is "groundbreaking and almost peerless."
Regin, as they've dubbed it, is malware that has been lurking in computers around the world for as long as six years, according to Symantec (SYMC), the cybersecurity firm that produces Norton Antivirus.
"Its capabilities and the level of resources behind Regin indicate that it is one of the main cyberespionage tools used by a nation state," Symantec said Sunday, explaining that "development took months, if not years, to complete."
The researchers said little to answer several key questions: Who designed it? How widely has it spread? What has it scooped up? What are the risks?
Related: Russian website streams thousands of private webcams
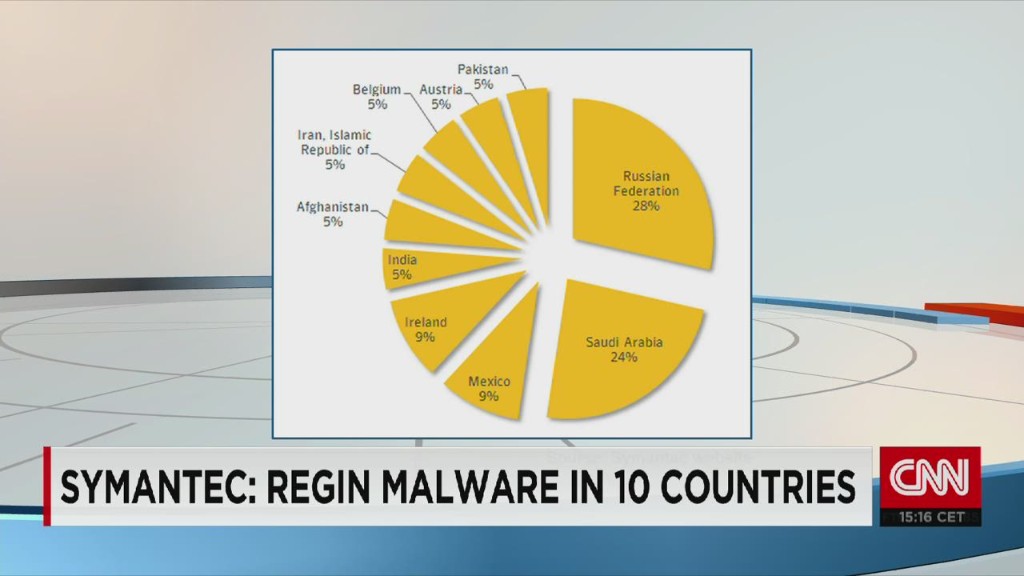
They said Regin has been discovered in at least 10 countries and was most heavily concentrated in Russia and Saudi Arabia.
The United States was not among the countries listed by Symantec.
The malware was installed on the computers of companies around the world, but it wasn't searching for business secrets. When a target was selected it searched airline computers to find out where the target was traveling. It scoured hotel computers to find his room number. And it tapped telecommunication computers to see who he was talking to.
"They were trying to gain intelligence, not intellectual property," said Symantec analyst Vikram Thakur.

Symantec said the malware conceals itself well and has several levels of protection. It uses multiple types of encryption, for example, and can communicate with the hacker that deployed it in several different ways.
It also uses a "modular" structure that conceals deeper layers of the malware and makes it "very difficult to ascertain what it is doing," researchers said.
In that respect, it is similar to the Stuxnet worm, which is widely believed to be a U.S.-designed weapon against the Iranian nuclear program. Iran is one of the 10 countries where Symantec says it found the Regin bug.
"Its low key nature means it can potentially be used in espionage campaigns lasting several years," it wrote, and additional components likely "remain undiscovered."
-- CNNMoney's Jose Pagliery contributed to this report

