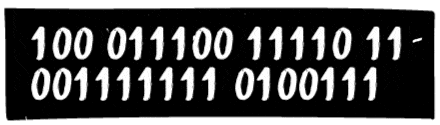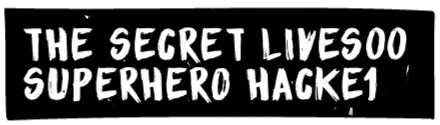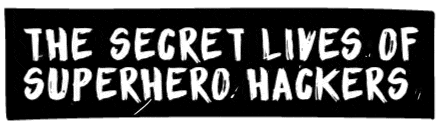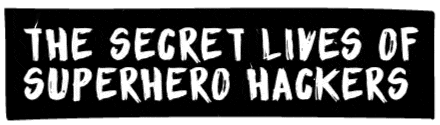
It's not easy being a spy.
Chris Inglis has worked in intelligence most of his adult life. He's tall, imposing and speaks with precision.
Debates about encryption technology -- like the ones that cropped up after last month's terror attacks in Paris -- are nothing new to him. Reports that ISIS is using apps with encryption tech to hide their conversations don't surprise him. He was the deputy director of the NSA and saw dozens of times when encryption was an obstacle in pursuing a target.
He couldn't get into specifics but explained broadly: The agency might identify an adversary through financial transactions, or by following the chain of possession for weapons. But if the target was using some form of encrypted messaging, the NSA would lose the last piece of the puzzle.
"The worst case scenario is that we fail to see a plot that essentially is on the fly ... and that we only see it when it's in execution," Inglis said. "At that moment in time, you're reacting to a disaster in the making as opposed to staving one off. That's the threat, that's the challenge."
Related: One on one with Anonymous
He's far from the first intelligence official to describe the problem -- both FBI Director James Comey and Matt Olsen, the former director of the National Counterterrorism Center, have been vocal on the dangers of encryption tech getting in the wrong hands.
Encryption is necessary to protect everything from email to banking. Coded messages protect dissidents from oppressive governments, aide workers in hostile environments, and average people at risk of being hacked. But an ever-growing list of apps -- WhatsApp, Telegram, Signal, Wickr, not to mention iMessage -- offer the ability to have encrypted conversations. That's been a game-changer for the intelligence community.
"The trend lines are heading to a place where those who would use these capabilities against us now realize ... that's a tool in their kitbag," Inglis said.

The nature of the game has also changed. Not long ago, adversaries used very different communications systems. It was appropriate, Inglis says, to try to hack into those because the exploit only hurt the enemy. Today, the bad guys are using the same tech as millions of innocent users. Meaning that if a security agency were to find a major security flaw, it's more important to patch it than to exploit it and collect information.
Related: This hacker knows if the government is spying on you
In the wake of Edward Snowden's revelations, debates have raged about whether government agencies should have backdoor access into encrypted conversations if there is reason to believe they contain a threat.
"I wouldn't call it a backdoor -- I think it's a pejorative term -- but a front door to appropriate authorities," Inglis said. "That is surgical. That is precise. It restricts the violation of privacy to only that situation."
Moxie Marlinspike, the hacker who designed the encryption technology used by Facebook (FB)-owned WhatsApp, says it will never work to give government agencies access.
"They're not capable of managing those secrets. They're getting hacked every day. It's not realistic to think that if they have the key to the kingdom, they're going to somehow be able to simultaneously use it, and keep it safe from China, or random hackers or other nation states."
Nevertheless, Inglis sees it as a matter of life and death: "We've all learned that we don't want to catch terrorists at the cockpit door."