
A new report shows which technology tools are being used by jihadists when they plot attacks against the West.
The free, mobile chatting service Telegram -- which is anonymous and encrypted -- is used by 34% of jihadists whose communications were the subject of a study by cybersecurity firm Trend Micro (TMICF).
Researchers monitored terrorist Internet forums and cataloged the listed contact information on 2,301 user accounts.
This study confirms previous research that ISIS uses Telegram to exchange secret messages. Telegram was started by a Russian tech entrepreneur who champions privacy and freedom.
Other free chatting apps popular with jihadists are Signal, Facebook's WhatsApp, and Wickr. Each is used by roughly 15% of jihadists. In their report, researchers said WhatsApp actually dropped in popularity after reports that investigators managed to make 16 arrests in anti-terror raids by spying on WhatsApp.
A small fraction of jihadists use lesser known chatting services, like surespot and Threema.
All offer encryption, which turns plain text conversations into jumbled code. This makes it extremely difficult -- sometimes impossible -- for government spies to conduct surveillance.
Indeed, experts say ISIS is getting harder to track.
FBI Director James Comey has warned this feature lets terrorists hide plans by "going dark." But the alternative -- limiting encryption -- has the self-defeating effect of putting everyday communication like banking and infrastructure at risk from hackers and terrorists themselves.
Then there's email.
Gmail is the standard email service used by 34% of jihadists, according to Trend Micro. This shows terrorists have simply gravitated toward the most popular email service in the world, which now has 1 billion users.
But that just hides a person's name. The FBI can still track down the physical location of a Gmail user by asking Google (GOOGL) to reveal the user's unique Internet Protocol address. Federal agents do this frequently.
Obscure email services called Mail2Tor and SIGAINT come in second and third place, each drawing roughly 20% of jihadists. These email services are particularly hard for law enforcement to track, because they operate within a realm of the Internet that's largely anonymous, Tor.
Tor is a system that encrypts and bounces Internet signals around the globe. It helps you evade censors when surfing the Web -- and it hides your computer's true location. In this case, Tor also hides who's using Mail2Tor and SIGAINT for email.
There's some evidence that the FBI has been able to hack Tor users to figure out their true location. But it's not known as a common tactic.
RuggedInbox and Yahoo (YHOO) Mail are less popular email options, according to researchers.
The Trend Micro study also looked at the unique, custom-built tools that jihadists built themselves to plot in secret.
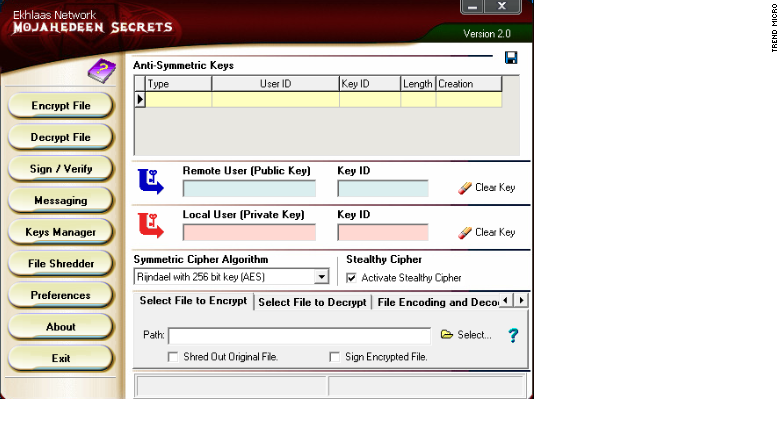
A tool called Mojahedeen Secrets, which encrypts email, was released in 2007 as an alternative to the popular privacy software PGP. It was the first professional-looking software made specifically for Islamic extremists. It's unclear who created it.
Jihadists also created a tool, called Asrar al-Dardashah, that easily latches onto the universal chatting software Pidgin. It lets them encrypt conversations between AIM, Google Talk, MSN, and Yahoo accounts.
There are established organizations that churn out this jihadist software, according to researchers.
In 2013, a group called the Global Islamic Media Front created an app called Tashfeer al-Jawwal, which encrypts mobile devices.
That same year, a group called the Al-Fajr Technical Committee developed a tool that encrypts email and text messages, Amn al-Mujahed.
Not everything is guaranteed to work, said cybersecurity expert Robert Graham.
It can be challenging for terrorists to build their own secrecy tools.
"Some of their tools are simple wrappers on existing [Western] tools. In other cases, it's new code, which is likely to get them caught," Graham said. "Even experts like me would be afraid of creating new cryptographic code."

