
A friendly woman on the internet can fool even the most security-conscious man -- and hackers can take advantage.
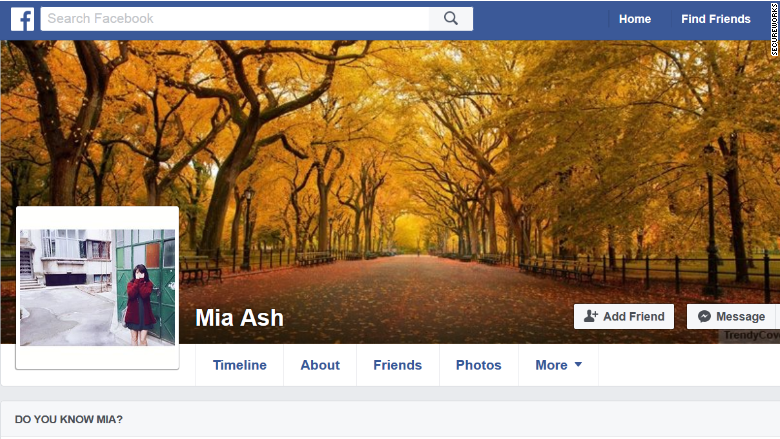
Since at least April 2016, a number of social media profiles have been created for a photographer named "Mia Ash." The persona befriended male employees of oil and technology firms in Israel, Saudi Arabia, India, U.S, and Iraq.
Now, a hacking group linked to Iran is believed to be behind the accounts, according to new research from security firm SecureWorks.
SecureWorks calls the hacking group Cobalt Gypsy, also known as OilRig by other researchers. The group has previously targeted Saudi Arabian oil, financial and tech executives, as well as Israeli corporate networks.
On LinkedIn, the hackers behind Mia connected with professional photographers to make the account seem more authentic. Meanwhile, the profile photos were stolen from a Romanian photographer, who has not responded to a request for comment.
Related: Saudi Arabia warns of new crippling cyberattack
The intent was to steal credentials from employees who would have access to their companies' computer networks. For example, the fake account sent a phishing email to one of the men she befriended containing malware. This would give the hackers control of his computer, SecureWorks found.
Mia first tried to befriend these individuals on LinkedIn, sharing information about her purported photography job and the trips she took. She later invited them to chat on other platforms like Facebook.
But the phishing attempt SecureWorks studied was unsuccessful. Although the the victim clicked on an infected link, the company's anti-virus precautions caught the malware.
As of now, the firm doesn't know if other attempts made by Mia were successfully executed. But it identified as many as 40 people who interacted with the persona on LinkedIn and Facebook (FB). Mia also had a personal photography website and fake accounts on Instagram, WhatsApp and Blogger. Most of those profiles are now offline.
According to Allison Wikoff, the lead researcher on the investigation into Cobalt Gypsy, LinkedIn can be a successful way for hackers to target people because users are inclined to trust others on the site. The hackers who posed as Mia used LinkedIn before switching to more personal communications channels like WhatsApp and Facebook.
"It's a professional network, so there's a little bit of trust people assume when they join it, versus social networks which are more designed for socialization," she said. "[Someone's] guard is a little more down on professional networks."
It's not the first time this group has used fake LinkedIn profiles to snare victims. In 2015, Cobalt Gypsy hackers posed as recruiters on the professional network. But using a single female persona was a first for this group.
In January, SecureWorks found that Cobalt Gypsy targeted a Middle Eastern company with phishing attacks that appeared to come from legitimate email addresses at a variety of information technology firms. Those phishing emails contained the same malware, called PupyRAT, Mia sent to her victim.
"Companies spend lot of time educating their staff on those kinds of phishing campaigns," Wikoff said. "So if that's not successful, establishing a personal relationship with your intended target is the best way to potentially make the connection."

