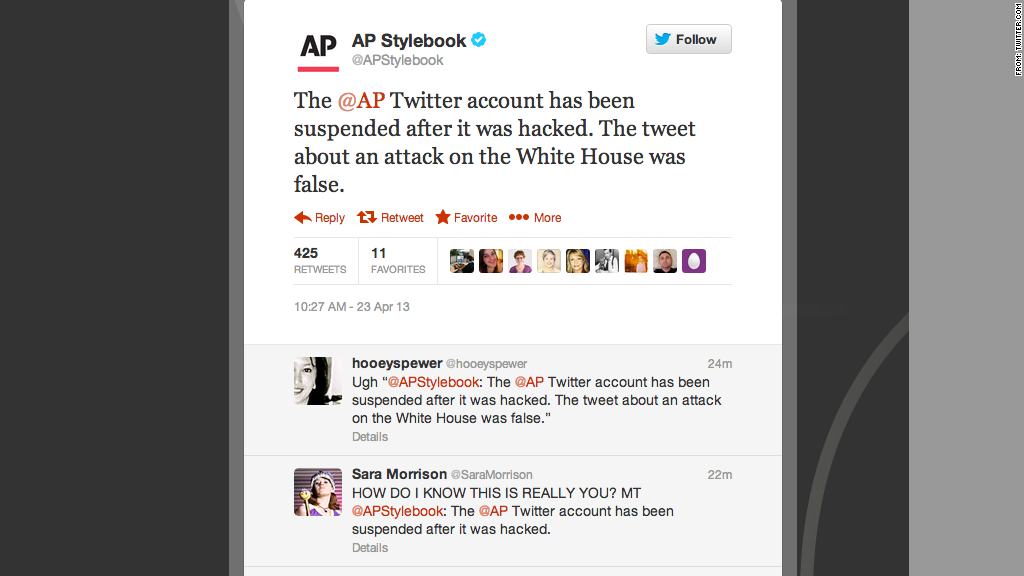
If Twitter needed any more evidence that it has a serious security problem, this should do it: Stocks plunged sharply on Tuesday after a hacker accessed a newswire's account and tweeted about a false White House emergency.
The shocking tweet came from the Associated Press earlier this afternoon: "Two Explosions in the White House and Barack Obama is injured."
The AP's communications team quickly tweeted from its own account that the main AP Twitter was compromised, but investors had already panicked. The Dow Jones industrial average (INDU) immediately plunged by more than 140 points.
And there it is: After years of hacks that typically involved little more than obscene language, Twitter's subpar security measures have now caused serious real-world consequences.
Many hacks happen when account owners use guessable passwords or access Twitter over public Wi-Fi and shared computers. If one person who tweets from a corporate account loses his or her phone, an entire corporation's Twitter account could be at risk.
The AP incident appears to be an example of social engineering. The news service posted a story Tuesday afternoon explaining that attackers gained access to the account after launching phishing attempts. When phishing, attackers pose as legitimate companies, such as Twitter, in an attempt for account holders to give up their passwords.
While Twitter can't control those issues, critics say the company could do more to prevent them.
Related story: Twitter's hacking problem
Security pundits have called on Twitter for years to beef up its security using simple methods: Sharply limit the login attempts allowed from a single IP address. Let only one person access a Twitter account at a given time.

Ideally, Twitter would employ a "two-factor authentication" login method. It's a basic security tool already used by Google (GOOG), Facebook (FB) and Dropbox that requires both a password and a piece of data, such as numbers sent via text message.
Twitter began posting job listings earlier this year for engineers to work on two-factor authentication. The posts came after Twitter's own systems were hacked, and the attackers gained access to usernames as well as encrypted and randomized passwords for about 250,000 users.
But job postings don't mean much until serious changes are implemented. Meanwhile, the hacks have continued. News organizations are a particularly attractive target thanks to their reach and influence.
The Twitter accounts of CBS' (CBS) 60 Minutes and 48 Hours were compromised over the weekend. In July 2011, News Corp.'s (NWS) Fox News account -- followed by more than 2 million people -- was hacked and tweeted that President Obama had been assassinated.
That same month, eBay's (EBAY) PayPal United Kingdom Twitter feed was hacked, and the profile photo was changed to a pile of excrement. Comcast's (CMCSA) NBC News account was also compromised two months later, falsely tweeting that a plane had crashed into the Ground Zero area of Manhattan.
In February of this year, both the Burger King (BKW) and Jeep Twitter accounts were hacked during the same week.
It's unclear what, if anything, Twitter plans to change. As always, a company spokesman said, "We don't comment on individual accounts for privacy and security reasons."
So far, Twitter has put the onus on brands to ensure they're being smart about choosing and sharing passwords. Following the Jeep account hack earlier this year, Twitter tweeted a link to a "friendly reminder about password security."
Twitter can tweet about best practices all it wants, but that approach clearly isn't working. When hacks do happen, the company does a good job of restoring compromised accounts typically within a few hours. But as the AP hack proves, these attacks can have damning real-world effects.

